IT-Security – the risks, challenges and solutions
The risks
To most companies, ransomware is a constant threat.
As the name indicates, ransomware is a software that takes over (parts of) an IT-installation with the aim of forcing the owner to pay a ransom to regain the command.
The problem is rapidly increasing these years. According to research by Cognyte, 1,097 organizations were hit by ransomware attacks in the first half of 2021. Compare this to 1,112 attacks for the entire year of 2020, and you have the number of attacks almost doubled.
This increase is mirrored in the latest predictions by Gartner. They expect at least 75% of IT organizations to have faced one or more attacks by 2025.
In order to mitigate the risk of having data hijacked, many have acquired advanced systems for detecting and preventing intrusion.
Various tools are available, but fundamentally the key is to have a well-architectured IT-network which is maintained and trimmed on an on-going basis.
The standard procedure is to have a firewall setup protecting the internal network.
This is brilliant for protection against hacking from outside. But often the threat comes from the inside, where malware is unconsciously introduced by employees.
Quite different measures are needed to mitigate that: Internal firewalls on servers, network segmentation, and separation of production environments from e.g. development- and test-environments.
Some standards require even more segmentation for the companies to be compliant e.g. PCI-DSS and GDPR.
The challenge
The task is to make sure that only the needed network traffic is allowed within the IT-network. Irrelevant traffic should not be allowed. This will reduce the probability for ransomware to spread inside the network, and thus provide a good protection.
Sounds simple, but there are some challenges:
- The complexity of the IT-network develops over time and the complexity will have an exponential increase as the number of attached units in the network increases.
- It is a huge task to differentiate between un-wanted and relevant network traffic.
- The traffic pattern for relevant – “normal” – traffic can change during the day, week, month.
- The relevant traffic pattern can change due to changes in business applications and changes in the network. Open port is a good example. They can have been relevant at one point in time, but later changes mean, that they are not used anymore. But are they then closed?
The solutions
The way to solve the problem is quite simple these days. It requires a basic discovery tool and some well-functioning processes.
- The discovery tool must be able to trace all IT-network traffic and be able to differentiate between relevant and unwanted traffic. The tool must further be able to detect openings in the network, which are not used, and therefore should be closed. e.g. open ports without any (relevant) traffic.
- It should be part of the deployment process and change process to define the changes in the traffic pattern, both between network units and the ports/protocols used.
- There must be an on-going “clean-up” process, which ensures, that openings not relevant/used, are closed.
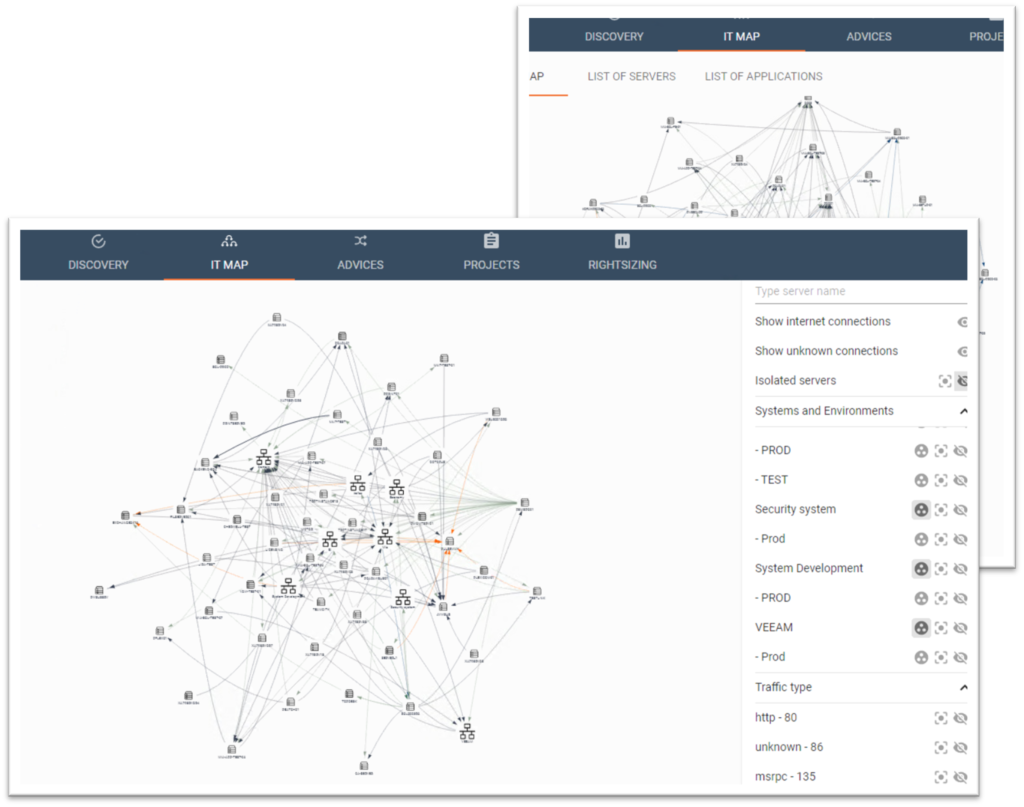
Transform data into information
At BOSCO we have designed a software for mapping an entire IT-installation into an intuitive overview. This enables our customers to track and monitor all IT-network traffic – not just in one frozen picture, but continuously over time: during the day, the week, and/or the month.
This enables our customers to…
- Reduce risk by implementing a network segmentation based on the actual traffic patterns
- Get solid input for establishing internal firewalls
- Avoid risky traffic between PROD-systems and e.g. TEST- and DEV-environments
- Clean up the IT-network and thus remove “Zombie”-units
…And architecture their IT-infrastructure:
- Make decisions on a true picture of their IT-setup
- Architecture their IT-Infrastructure based on the real entities and relations